Fwd: Alison Ledgerwood -- Getting stuck in the negatives (and how to get unstuck)
(German) Krautreporter bleiben (oder werden)
Hallo! Von Krautreporter hatte ich parallel über meinen Bruder und durch die "Jung & Naiv" Videos von Tilo Jung erfahren. Mit meiner Mitgliederschaft als Leser bin ich sehr zufrieden: Viele Extras habe ich nicht genutzt, aber doch hier und da in einen Mitglieder-only-Podcast ("Viertel vor Feierabend") reingehört und auch die Gelegenheit genutzt, die Redaktion zum Jubiläum vor Ort etwas näher kennenzulernen. Ich bin auf jeden Fall im zweiten Jahr dabei, nicht als Experiment sondern wegen der Artikel: viel Spannendes dabei. Spannend fand ich persönlich zum Beispiel konkret
- Nico Grimm — Was hindert die Türkei eigentlich daran, das Wort Völkermord zu akzeptieren? Andere haben es doch auch geschafft.
- Frank Seibert — "Der ganze Berg, dieser ganze scheiß Berg ist vor mir zusammengebrochen",
- die Interview-Videos von Danijel Višević — Krieg im Kopf: Warum Soldaten nach Einsätzen krank werden
und von Theresa Bäuerlein hab ich noch mehrere Bookmarks mit Artikeln, für die ich mir noch Zeit nehmen werde. Ich hoffe sehr, dass Krautreporter weiter bestehen kann. Vielleicht ist echter Journalismus ohne Werbung ja auch was für dich? Mehr Details gibt's hier:
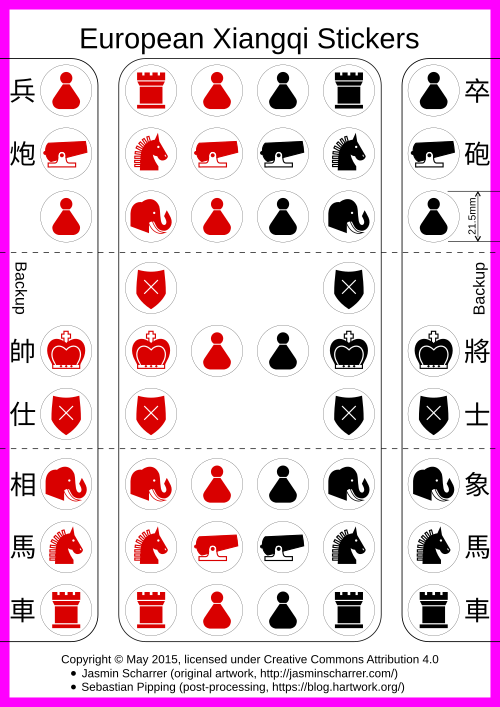
European Xiangqi stickers (Chinese chess)
Hello! For quite a while I have been looking for someone to design european piece graphics for Xiangqi (Chinese chess) without luck. Early this March I was pointed to Jasmin Scharrer fortunately! The pieces she designed allowed making sheets of stickers to help kickstart the learning experience of people new to the game, facing Chinese- only gaming hardware: You put stickers on the backside of the pieces and turn them over whenever you are ready to: only some and then some more, all at once, your choice. This is the stickers on real hardware:
The full sticker sheet takes an A4 page and looks like this:
To print your own, you should use the vector version for quality. Since we picked CC-BY-4.0 for a license, you could even sell your prints as long as proper attribution to
Jasmin Scharrer (original artwork, <https://jasminscharrer.com/>), Sebastian Pipping (post-processing, <https://blog.hartwork.org/>)
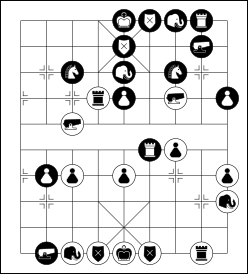
for the initial source is done. Using the same piece graphics, xiangqi- setup also has a piece theme "euro_xiangqi_js" now. With that, you can render European setup images like this one:
$ xiangqi-setup --pieces euro_xiangqi_js --width-cm 7 \ doc/demo.wxf output.svg
If you need help with any of this or for feedback in general, please feel free to contact me at sebastian@pipping.org.
Best, Sebastian
gentoo.de relaunched
Hi! Two months ago, the gentoo.org website redesign was announced. For a few hours now, gentoo.de is following. The similarities in look are not by coincidence: Both design were done by Alex Legler. The new website is based on Jekyll rather than GuideXML previously. Any bugs you find on the website can be reported on GitHub where the website sources are hosted. I would like to take the opportunity to thank both Manitu and SysEleven for providing the hardware running gentoo.de (and other Gentoo e.V. services) free of charge. Very kind! Best, Sebastian
(German) Fwd: Gentoo-Workshop Samstag 01.08.2015 Troisdorf (nahe Köln/Bonn)
Hallo! Die Troisdorfer Linux User Group (kurz TroLUG) veranstaltet am Samstag den 01.08.2015 in Troisdorf nahe Köln/Bonn einen Gentoo-Workshop, der sich an fortgeschrittene User richtet. Mehr Details, die genaue Adresse und der Ablauf finden sich auf der entsprechenden Seite der TroLUG.
Grüße, Sebastian
uriparser 0.8.2 released
I'll just dump the change log diff here for now.
2015-04-27 -- 0.8.2 * Fixed: Broken conversion from/to Windows network shares (bug #21) Thanks to Adam Gross and Dmitry Repkin! * Fixed: Limit uriCompareRange return values to -1/0/1 (bug #24) As a side effect, this fixes the test suite for AArch64. Thanks to Marcin Juszkiewicz for the patch! * Fixed: MinGW Makefile: LIB_DIR fixed from ../../lib leftover to ../../src (bug #27) Thanks to Dmytro Zagashev for the report! * Fixed: Add missing NULL checks to UriStringToFilename (bug #25) Thanks to Jerome Custodio for the report! * Changed: Leave inlining decisions to GCC * Soname: 1:18:0
https://sourceforge.net/projects/uriparser/
Yes, I still need to get it off SourceForge...
Comment vulnerability in Wordpress 4.2
Hanno Böck tweeted
about WordPress 4.2 Stored XSS rather
recently. The short version is: if an attacker can comment on your blog, your
blog is owned. Since the latest release is affected and is the version I am
using, I have been looking for a way to disable comments globally, at least
until a fix has been released. I'm surprised how difficult disabling comments
globally is. Option "Allow people to post comments on new articles" is filed
under "Default article settings", so it applies to new posts only. Let's
disable that. There is a plug-in Disable
comments,
but since it claims to not alter the database (unless in persistent mode), I
have a feeling that it may only remove commenting forms but leave commenting
active to hand-made GET/POST requests, so that may not be safe. So without
studying Wordpress code in depth my impression is that I have two options:
- a) restrict comments to registered users, deactivate registration (hoping that all existing users are friendly and that disabled registration is waterproof in 4.2) and/or
- b) disable comments for future posts in the settings (in case I post again before an update) and for every single post from the past.
On database level, the former can be seen here:
mysql> SELECT option_name, option_value FROM wp_options WHERE option_name LIKE '%regist%'; +----------------------+--------------+ | option_name | option_value | +----------------------+--------------+ | users_can_register | 0 | | comment_registration | 1 | +----------------------+--------------+ 2 rows in set (0.01 sec)
For the latter, this is how to disable comments on all previous posts:
mysql> UPDATE wp_posts SET comment_status = 'closed'; Query OK, .... rows affected (.... sec) Rows matched: .... Changed: .... Warnings: 0
If you have comments to share, please
usee-mail this time. Upgraded to 4.2.1 now.
Apache AddHandler/AddType vulnerability: Magento
I ran into an example of a web application vulnerable to Apache AddHandler/AddType misconfiguration by chance today. The releases notes of Magento Community Edition 1.9.1 point to a remote code execution vulnerability.
Interestingly, the section
Determining Your Vulnerability to the File System Attack
is precisely a switch from AddHandler to SetHandler. Fantastic! Let's see
if I can use that to convince web hoster X that is still arguing that use of
AddHandler would be good enough.
PS: Before anyone takes this for advice to switch to vanilla 1.9.1.0, be sure to apply post-release easy-to-overlook patch "SUPEE-5344", too. Details are up at (German) Magento-Shops stehen Angreifern offen or (English) Analyzing the Magento Vulnerability.
(German) Fwd: Petition gegen Vorratsdatenspeicherung
Ich bin ehrlich gesagt irritiert, dass wir diese dumme Idee schon wieder aufgekommen ist. Bitte mit-unterschreiben
https://www.change.org/p/heiko-maas-bundesregierung-stoppen-sie-die- vorratsdatenspeicherung-vds
und weiter verteilen. Danke!
Firefox: You may want to update to 37.0.1
I was pointed to this Mozilla Security Advisory:
Certificate verification bypass through the HTTP/2 Alt-Svc header https://www.mozilla.org/en-US/security/advisories/mfsa2015-44/
While it doesn't say if all versions prior to 37.0.1 are affected, it does say that sending a certain server response header disabled warnings of invalid SSL certificates for that domain. Ooops. I'm not sure how relevant HTTP/2 is by now.